Tag: hacking
Learning About Stack Smashing Exploits
by admin on Jul.16, 2009, under Linux, My Life
It seems we are always reading update notes saying:
“Fixed a potential buffer overrun condition which if exploited could result in the attacker executing arbitrary code and possibly escalating privileges.”
These exploits are extremely common, and of course patches and updates to correct such are equally common, regardless of the OS platform.
I of course had a generalized understanding of how these exploits worked – but I’ve recently decided to really dive in and greatly increase my knowledge in this area. A superficial understanding was no longer sufficient and I wanted to not only understand better, I wanted to learn how to leverage such exploits with hands on hacks.
So – I armed myself with some material, starting with “Hacking: The Art of Exploitation” by Jon Erickson loaned by a colleague. As it turned out the first edition of this book was published in 2003. Since then there have been many changes in both gcc and recent versions of the 2.6 kernel that greatly improve stack security. Thus the sample code in the book is no longer capable of simply being compiled and executed to achieve the desired result.
I ended up learning just as much getting the first exploits to work correctly in more modern distros as from the text itself. But its all part of the educational process and I certainly understand the current kernel and gcc operations a bit better. And I was able to make the first lessons work.
Making Old Hacks Work
The best way I found to get the code to compile and run as intended was to use an older OS and Kernel in Virtual Box. I installed a basic install of Ubuntu 6.06 and used that. The 6.2.15 kernel it had allowed the exploits to run, if you tweaked it.
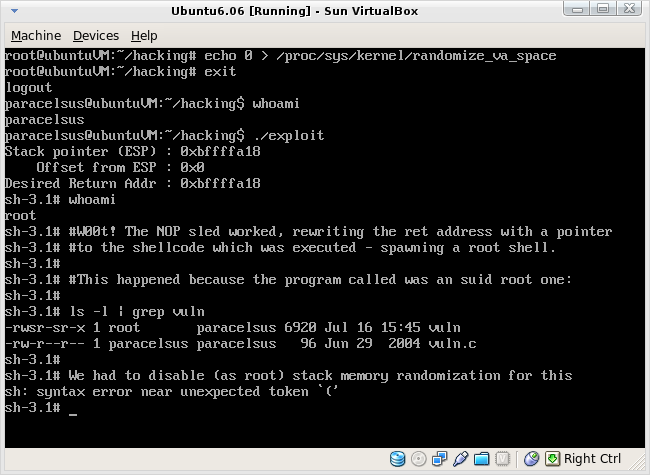
By disabling randomize_va_space in /proc/sys/kernel and by compiling with an earlier version of gcc (3.3 and 4.0) the results were achieved:
The exploit is a simple one, but a classic. It simply rewrites the return address by over flowing the buffer, taking control of the execution flow of the program that calls it and directing it to run a snip of shellcode. The shellcode is a self contained piece of assembly that spawns a shell. Because the program that is called is an suid root program, and runs as root, a root shell is opened. (Note there are several suid binaries installed on most systems and a similar exploit against any of them could potentially achieve the same.)
The source for the two programs for this exploit can be found here and here.
(Ensure vuln is owned by root and has the suid bit set with chmod +s)
To Learn More
I recommend the new second edition of Hacking The Art of Exploitation by No Starch Press, which you can review here. The new version looks like it takes more modern compiler and kernel design into account and has expanded content as well.
Current GCC and Kernel Operation
Note that more recent versions of gcc (4.2 and higher I believe) compile with stack protection enabled by default. To compile without use:
user@system:~/$ gcc-4.3 -fno-stack-protector -o exploit exploit.c
Also, you may find reading up on stack protection and the following kernel options to be helpful:
root@paracelsus-laptop:~/hacking# cat /proc/sys/vm/mmap_min_addr
0
root@paracelsus-laptop:~/hacking# cat /proc/sys/vm/vdso_enabled
0
root@paracelsus-laptop:~/hacking# cat /proc/sys/kernel/randomize_va_space
0