My Life
PHPChain Password Manager
by admin on Feb.19, 2010, under Linux, My Life
NOTE: Since the original post I discovered a new version of PHPChain is available at the project Sourceforge site here. You may test drive it here. The new version has several additional features and the issues with the underlying PHP code described below have been corrected. I had no issues running the new version with PHP 5.3. Unfortunately, there is no way to easily migrate your database from the old version, but the new version does allow the import and export of data in XML format.
PHPChain is a great little app which helps you organize passwords. It uses a web interface, encrypts the passwords in a MySQL database, and supports multiple users, each with their own account. Passwords are organized in user defined groups, and are easy to edit. It automatically alphabetizes entries, helping to organize them further. The interface is extremely easy to use, and it makes storing and organizing you many passwords very easy. You can try a demo of it here.
I opted for this as a solution to store my passwords at home. It provided the added benefit of having access to my passwords from anywhere over an SSL web site. While there may be some slight risk in this, lets be honest — it is a hell of a lot better than the open office document I was using before. And of course you can further protect it by only opening the port it listens on when needed, and even place it behind an .htaccess, etc. You can be as paranoid as you like.
The one thing is that this application does not appear to have been updated in a while, and if you install it today you may run into a situation where PHP does not read some of the scripts as the author used php short tags
Here are some notes that might help you with your install.
First of course you will need to install apache with the necessary php and ssl packages, as well as php5-mcrypt installed. You will also need to generate a self signed SSL certificate and set up a vhost that will accept SSL connection. You certainly want to use SSL, even if you intend to only access this on you local network as otherwise all traffic will be sent clear text, which would be bad. Setting up apache to use a self signed SSL is pretty straight forward and there are lots of sites for your distro to guide you in this.
At a minimum you will need things like:
apache2-2.2.13-2.3.1.i586
apache2-mod_php5-5.3.0-2.4.3.i586
openssl-0.9.8k-3.4.i586
apache2-mod_php5-5.3.0-2.4.3.i586
php5-mcrypt installed
php5-mysql-5.3.0-2.4.3.i586
Once you download PHPChain, simply extract it in your web document root and create and empty MySQL database, them import the .sql file into it. See the README.txt for details. If you access it now, you will likely see lots of messages as some scripts are not being parsed correctly due to the short tags being used. Find which ones this are by:
Callandor:/srv/www/htdocs/phpchain # grep -R ” ./cat.php: ./inc/menu.php: ./inc/db.php: ./inc/cookie.php: ./inc/header.php: ./inc/header.php:PHPChain – Powered by PHPChain
./inc/header.php: ./inc/header.php: ./inc/header.php: ./inc/header.php: ./inc/crypt.php: ./inc/form.php: ./index.php: ./login.php: ./logout.php: ./newlogin.php: ./password.php: ./settings.php:
Change all instances of the
Callandor:/srv/www/htdocs/phpchain # sed “s/> testchange; sed “s/> testchange
To virst view the changes in each file, and then if it looks good replace with:
Callandor:/srv/www/htdocs/phpchain # sed -i “s/
Or, to be even fancier with it . . .
Callandor:/srv/www/htdocs/phpchain # for i in `grep -R “
Now, the php should work correctly, but you will likely have some warnings dispalyed at the top of the page regarding some constant variable declarations. You can disable php warning by setting the error_reporting level on a per script basis. Turn off errors and warnings in index.php (before the include statements) by adding:
error_reporting(0);
Or set the error reporting level in you php.ini
That should do it, you an now start using PHPChain to manage your passwords in a more secure way. Do ensure to use SSL, and if you connect without SSL PHPChain conspicuously warns you of the danger of this.
Xbash Art and Music Fest
by admin on Jul.19, 2009, under My Life
So I checked out the X Bash 09 and it was pretty cool. Its an annual music/art festival, sort of Burning Man-esque, held at a clothing optional resort north of Tampa.
Highlights where:
* Randy’s Burning Man camp (OBE: Our of Body Experience) and his mobile art cars. One was a golf cart with a tropical themed bed (with parasol) all around it – so he could drive his bed around Burning Man. He was a cool guy and lit up his large camp dome at night with spinning floral patterns.
* A glass artist who made really beautifully patterned pieces (mostly pipes). The coloration and patterns where awesome. He did demonstrations too – while naked – which was a trip (mind that torch!)
* There were several bands and DJs but the two I found most interesting where Syncrisis and Professional Astronauts. Syncrisis played a good set, they had a good developed sound and I liked the style. Professional Astronauts sounded pretty similar to System of a Down – it was hillarious when they played “Arabian Nights” from Disney’s Aladin – you can imagine how that sounded. Both were well recieved by the crowd and you can catch them playing around the Tampa scene.
* There were some dancers after the bands who danced during DJ Chaos’ set – pretty fun to watch. One was dressed like a mange she-devil, etc.
I had hoped there would be more artists there as it seems like a great alternative venue for attracting them, but unfortunately I only saw a few (there were likely others there on other days as it was a 3 day event.)
The event was hosted by Xanthia, she was very nice and showed me a new painting she was working on and had some other pieces around, but was not there to display her work in particular but host the event in general. Her studio is there as well and she is an artist in several media. She has some pretty cool stuff and you can check it out at:
The annual event is hosted at naturlist resort (The Riverboat Nudist Resort) and is clothing optional. The croud was predominately in their 20s and 30s, with some older and youger as well. Most people were clothed, but the idea is all about self expression so many were partially or fully unclothed as well. There was a bubble pit that got going later on and lots of people seemed to like that – it would have a dozen or so people in it at any time, and it is just behind the dance floor in front of the stage. Super sticky bubbles are hard not to like.
This was a pretty cool event and with a bit more promotion could be huge. The have camping facilities and many spaces where artists or groups to get together to do their own thing. It was great having the bands and DJs there, and it would be great to see more artists display there.
Learning About Stack Smashing Exploits
by admin on Jul.16, 2009, under Linux, My Life
It seems we are always reading update notes saying:
“Fixed a potential buffer overrun condition which if exploited could result in the attacker executing arbitrary code and possibly escalating privileges.”
These exploits are extremely common, and of course patches and updates to correct such are equally common, regardless of the OS platform.
I of course had a generalized understanding of how these exploits worked – but I’ve recently decided to really dive in and greatly increase my knowledge in this area. A superficial understanding was no longer sufficient and I wanted to not only understand better, I wanted to learn how to leverage such exploits with hands on hacks.
So – I armed myself with some material, starting with “Hacking: The Art of Exploitation” by Jon Erickson loaned by a colleague. As it turned out the first edition of this book was published in 2003. Since then there have been many changes in both gcc and recent versions of the 2.6 kernel that greatly improve stack security. Thus the sample code in the book is no longer capable of simply being compiled and executed to achieve the desired result.
I ended up learning just as much getting the first exploits to work correctly in more modern distros as from the text itself. But its all part of the educational process and I certainly understand the current kernel and gcc operations a bit better. And I was able to make the first lessons work.
Making Old Hacks Work
The best way I found to get the code to compile and run as intended was to use an older OS and Kernel in Virtual Box. I installed a basic install of Ubuntu 6.06 and used that. The 6.2.15 kernel it had allowed the exploits to run, if you tweaked it.
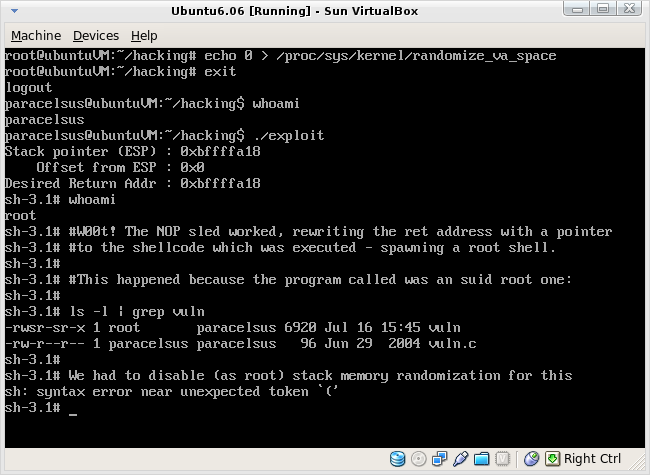
By disabling randomize_va_space in /proc/sys/kernel and by compiling with an earlier version of gcc (3.3 and 4.0) the results were achieved:
The exploit is a simple one, but a classic. It simply rewrites the return address by over flowing the buffer, taking control of the execution flow of the program that calls it and directing it to run a snip of shellcode. The shellcode is a self contained piece of assembly that spawns a shell. Because the program that is called is an suid root program, and runs as root, a root shell is opened. (Note there are several suid binaries installed on most systems and a similar exploit against any of them could potentially achieve the same.)
The source for the two programs for this exploit can be found here and here.
(Ensure vuln is owned by root and has the suid bit set with chmod +s)
To Learn More
I recommend the new second edition of Hacking The Art of Exploitation by No Starch Press, which you can review here. The new version looks like it takes more modern compiler and kernel design into account and has expanded content as well.
Current GCC and Kernel Operation
Note that more recent versions of gcc (4.2 and higher I believe) compile with stack protection enabled by default. To compile without use:
user@system:~/$ gcc-4.3 -fno-stack-protector -o exploit exploit.c
Also, you may find reading up on stack protection and the following kernel options to be helpful:
root@paracelsus-laptop:~/hacking# cat /proc/sys/vm/mmap_min_addr
0
root@paracelsus-laptop:~/hacking# cat /proc/sys/vm/vdso_enabled
0
root@paracelsus-laptop:~/hacking# cat /proc/sys/kernel/randomize_va_space
0
Toorcamp: Taking the Hack Underground
by admin on Jul.04, 2009, under IT Adventures, Linux, My Life
(You can find the first post here with a bit more info.)
After the Toorcamp officials negotiated it out, the owner (collectively known as Mr. Ass-Wee-Pay) finally allowed access to the missile silo today. This made a huge difference in the whole experience at Toorcamp. Otherwise, as my brother so perfectly put it, the event was a bit like:
“Come to a hacker fest at an abandoned nuclear silo!*”
(*Silo not included)
Fortunately all this changed today, and the site was fully opened to workshops, talks and tours. Way to go Toorcamp guys!
It was utterly awesome. While camping on the surface was pretty un-enjoyable with the extreme dust and heat, the silo was completely different. The temperature was easily 25-30 degrees F less in the silo. In fact you could only stay about 2 hours before you would become uncomfortably cold and want to return to the surface. Good thing I thought ahead enough to bring a fleece pull over to the desert!
I took many, many pictures of the silo and will cull a few of the best for this blog post, and others can be found on my gallery.
The Titan Missile Silo:
The entrance was a steel and concrete hatch easily a foot think. It was propped up (literally) on supports, themselves not bolted down. The ingress / egress safety briefing included strict instructions not to touch the hatch in any way. Think of a rabbit trap made out of a box and you get the idea.
You then proceeded down a very narrow passage and flight of stairs, forcing a single person to enter. This was engineered to allow a guard to be able to hold back any number of people attempting to infiltrate the entrance. A 10 year old with a slingshot could defend this entrance.
After this, at about 20 feet down you entered the main lift tower. The elevator of course was long since removed, so you descended the five flights of stairs – sturdy and steel plated until you arrived at the bottom of the lift and the main entrance. Here tunnels ran off in four directions. Two lead immediately into the control and power domes.
The power dome (above) was massive, originally housing the generators. A section of the ceiling of this dome had been opened (after being excavated) to allow access to the facility and removal of the generators and other equipment. All other parts of the facility are still completely buried. The moss growing is due to the ceiling being open to the sky.
(Just click below to read more.)
Live From Toorcamp
by admin on Jul.03, 2009, under IT Adventures, Linux, My Life, Netbooks, Sago Labs
[Want to see the pictures? They are here!]
Kyle and I arrived to Seattle late Wednesday and my brother Robert picked us up. After staying the night at his place we got up Thursday morning and road tripped across the cascades toward Moses Lake. The trip through the mountains was very nice, with beautiful scenery. I’ve not been in the cascades in over 20 years, and it was a plesent change of scenery from my current Tampa bay scenery.
We navigated easily to the site, about :35 outside of town. The environment is farmland, with crops (hey and alfalfa it seems) stretching into the horizons. It is semi-arid and pretty hot, in the low 90’s, and extremely dusty.
First thing on arrival: Assemble and solder your camp pass – a few resisters and two LEDs on a PCB with an inducer – then test by swipping in front of a credit card reader. Blink blink, you are a go.
Presentations yesterday and the Ignite! Toorcamp talks last night were very good – ranging from OSX & Linux stack protection and memory randomization in compiled apps, a Spacepunk talk showing low earth photos taken with a home constructed satellite made with a Sony cybershot camera and deployed via balloon by Hackerbot Labs – they are on site and I’ll be seeing them for more info on this! Also a very interesting talk by Psychesonics on binomial sound waves to sync brain wave activity – hack your mind.
We went to town this morning for supplies, returning for the first talks. I’m sitting in an iptables firewall class now, to be followed by muti-channel bluetooth hacking and then SQL injection.
Bad news: Apparently camp coordinators did not have a contract with explicit access rights to the Missile Silo itself, leaving all authority up to the discretion of the owner. This is bad. As a result, before the conference even started some guys went into the silo unauthorised, the owner paniced and decided to revoke ALL access to the Silo yesterday – so all the talks yesterday that were to be given underground were given on the surface instead. Now, the owner has so graciously allowed one group of people so far to tour the underground silo. It is unknown yet if there will be more tours offered.
Moral of the story: When hosting an event at speciality locations, get a contract to ensure your access rights, etc. Otherwise – just use the national forest which costs nothing and has full public access rights. And it’s a hell of a lot more comfortable environmentally in the mountians!
But the conference itself, the data and the attendees are all very interesting and entertaining and there is a lot more goodness yet to come.
Will update more later.